Denial-of-Service Attacks
Customers can call the coffee shop to place their orders. After answering each call, a cashier takes the
order and gives it to the barista.
However, suppose that a prankster is calling in multiple times to place orders but is never picking up
their drinks. This causes the cashier to be unavailable to take other customers’ calls. The coffee shop can
attempt to stop the false requests by blocking the phone number that the prankster is using.
In this scenario, the prankster’s actions are similar to a denial-of-service attackDenial-of-Service Attacks
A denial-of-service (DoS) attack is a deliberate attempt to make a website or application unavailable to users
For example, an attacker might flood a website or application with excessive network traffic until the
targeted website or application becomes overloaded and is no longer able to respond. If the website or
application becomes unavailable, this denies service to users who are trying to make legitimate
requests.
Distributed Denial-of-Service Attacks
Now, suppose that the prankster has enlisted the help of friends.
The prankster and their friends repeatedly call the coffee shop with requests to place orders, even
though they do not intend to pick them up. These requests are coming in from different phone numbers,
and it’s impossible for the coffee shop to block them all. Additionally, the influx of calls has made it
increasingly difficult for customers to be able to get their calls through. This is similar to a distributed
denial-of-service attack.
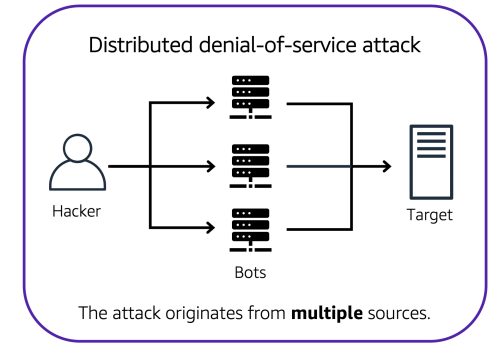
In a distributed denial-of-service (DDoS) attack, multiple sources are used to start an attack that aims to
make a website or application unavailable. This can come from a group of attackers, or even a single
attacker. The single attacker can use multiple infected computers (also known as “bots”) to send
excessive traffic to a website or application.
To help minimize the effect of DoS and DDoS attacks on your applications, you can use AWS Shield.
Author: Mohit T

No comments:
Write commentsPlease do not enter spam links